Access to torrent platforms has become increasingly restricted across multiple countries due to copyright enforcement, ISP blocking, and domain seizures. As a result, users frequently search for alternative ways to reach formerly popular torrent indexes. While accessing such platforms raises important legal and security considerations, various technical methods are commonly discussed online as ways to bypass basic restrictions. Understanding how these techniques function — along with their risks — is essential before attempting any form of access.
TLDR: Many torrent indexing sites face ISP blocks or domain restrictions in 2025, leading users to seek alternative access methods. Common techniques include proxy mirrors, VPN services, Tor access, DNS modifications, and decentralized options. However, each method carries legal, ethical, and security implications that should be carefully considered. Safe browsing practices and understanding local laws remain critical before attempting access.
- Why Torrent Sites Face Blocks in 2025
- 7 Methods Commonly Used to Unblock Torrent Platforms
- Security Considerations When Accessing Torrent Platforms
- Legal and Ethical Implications
- Best Practices for Safer Browsing
- The Changing Landscape of Torrent Access in 2025
-
Frequently Asked Questions (FAQ)
- 1. Is using a proxy site illegal?
- 2. Does a VPN make torrenting completely anonymous?
- 3. Why are torrent domains frequently changing?
- 4. Is changing DNS enough to bypass restrictions?
- 5. Are proxy mirrors safe to use?
- 6. What is the safest way to obtain digital media?
- 7. Why is torrent access slow when using certain networks?
Why Torrent Sites Face Blocks in 2025
Internet Service Providers (ISPs) in many regions block torrent indexing domains following court orders or regulatory mandates. These blocks typically operate through:
- DNS filtering
- IP address blocking
- Deep Packet Inspection (DPI)
- Domain seizures
In most cases, the block does not mean the platform disappears entirely — only that access from certain networks becomes restricted.
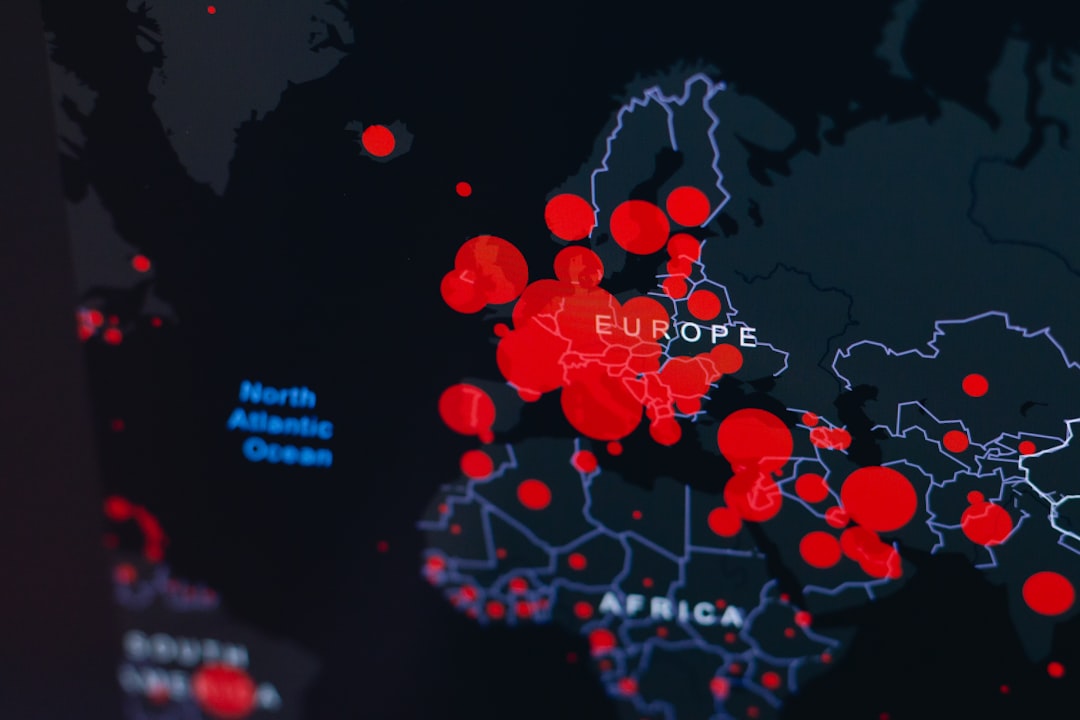
Users attempting to bypass these measures often focus on technical rerouting methods rather than direct domain access. Below are seven commonly referenced approaches in 2025.
7 Methods Commonly Used to Unblock Torrent Platforms
1. Proxy Mirror Sites
Proxy mirrors replicate the original site’s database and interface under a different domain. These mirrors are hosted in jurisdictions where enforcement is less aggressive or where blocks have not yet been implemented.
Key Considerations:
- Mirrors may contain malicious ads or injected scripts.
- Authenticity is difficult to verify.
- Availability changes frequently.
Because there is no official verification system, users are often exposed to phishing attempts or malware. Security precautions are critical when browsing mirror domains.
2. Virtual Private Networks (VPNs)
A VPN encrypts internet traffic and routes it through a remote server, potentially bypassing ISP-level blocks. In 2025, VPN usage remains one of the most widely discussed privacy tools.
- Encrypts browsing activity.
- Masks local IP address.
- Can bypass regional restrictions.
However, legality varies by country, and using VPNs for copyright infringement may still result in legal consequences. Not all VPNs provide equal privacy protections.
3. The Tor Network
The Tor browser routes internet traffic through multiple nodes, anonymizing user activity. Since traffic is distributed and encrypted, ISP-level blocking is often ineffective.
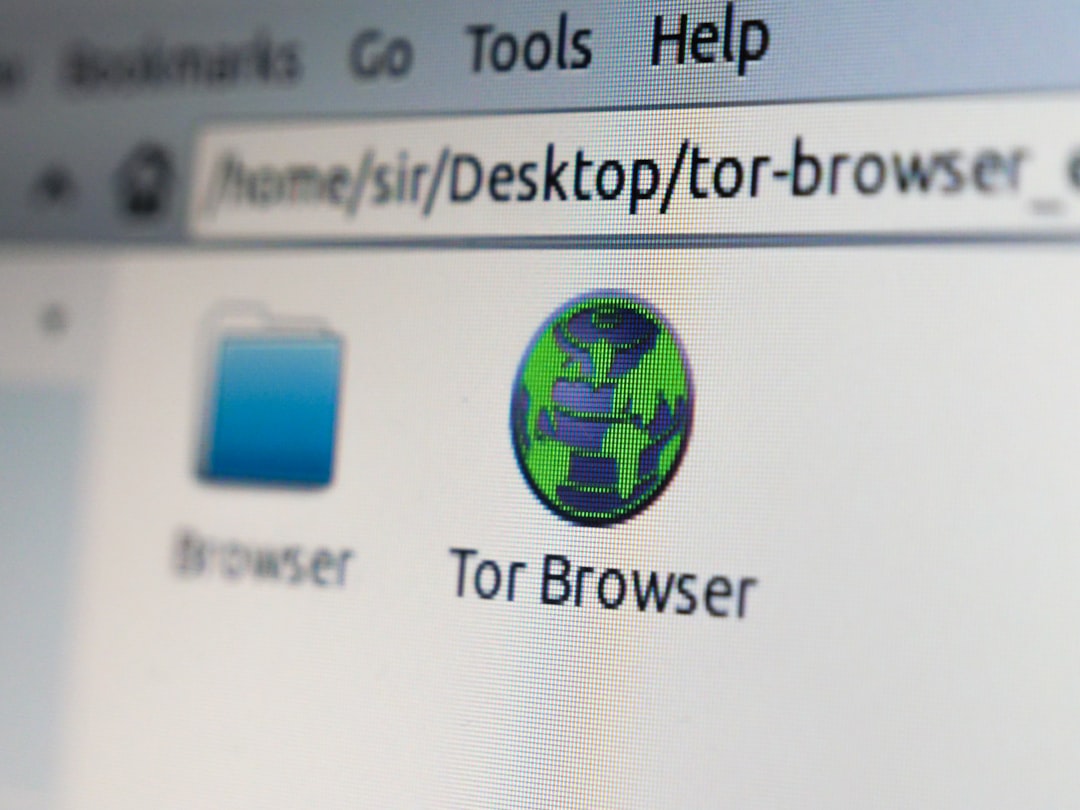
Limitations include:
- Slower browsing speeds.
- Possible exit-node monitoring risks.
- Occasional mirror inaccessibility.
Tor prioritizes anonymity but does not eliminate legal risks associated with copyrighted material.
4. Changing DNS Providers
Some ISP blocks rely solely on DNS filtering. Switching to a public DNS resolver may bypass these restrictions.
- Simple configuration change.
- Works against DNS-only blocks.
- Limited effectiveness if IP-level blocking is active.
This approach does not provide encryption or anonymity on its own.
5. Web-Based Access Tools
Web-based proxy tools load content through an intermediary website. These tools allow limited page access without directly connecting to the blocked domain.
Risks include:
- Data interception.
- Advertisement injection.
- Session hijacking vulnerabilities.
Such methods may grant temporary access but often compromise security.
6. Decentralized Torrent Indexing Alternatives
Some newer torrent indexing solutions operate using decentralized technology, reducing reliance on a single domain. These include distributed magnet-based directories or peer-to-peer index lookups.
Advantages:
- Harder to shut down.
- No central server.
Disadvantages:
- Technical learning curve.
- Limited content verification mechanisms.
7. Browser Extensions With Integrated Proxies
Certain browser extensions reroute traffic through proxy nodes automatically. While convenient, they present notable privacy concerns.
- Limited encryption strength.
- Unknown logging policies.
- Potential data resale practices.
Users should thoroughly evaluate extension permissions and user reviews before installation.

Security Considerations When Accessing Torrent Platforms
Beyond access methods, security remains the primary concern in 2025.
Malware and Fake Torrents
Malicious actors often upload files disguised as legitimate downloads. These may contain ransomware, keyloggers, or trojans.
Data Logging and Monitoring
Even with rerouting methods, certain services keep logs. If subpoenaed, those logs may expose user data.
ISP Monitoring
In jurisdictions where torrent surveillance is active, ISPs may log peer-to-peer traffic. Using encryption alone does not necessarily prevent traffic analysis.
Legal and Ethical Implications
Accessing torrent indexing platforms is not inherently illegal; legality depends on jurisdiction and the nature of content downloaded. Downloading or distributing copyrighted material without authorization may violate local laws.
Before attempting to access any blocked resource, individuals should:
- Review their country’s copyright regulations.
- Understand ISP policies.
- Consider legitimate alternatives such as licensed streaming or open-source repositories.
Best Practices for Safer Browsing
- Use updated antivirus software.
- Avoid downloading executable files when unnecessary.
- Check file comments and verification indicators carefully.
- Limit sharing of personal data.
- Enable firewall protection.
No method guarantees perfect security or anonymity. Awareness and caution remain the most effective protections.
The Changing Landscape of Torrent Access in 2025
Authorities continue refining blocking technologies, while users experiment with alternative routing and decentralization methods. The result is an ongoing technical cycle of restriction and adaptation.
However, increasing emphasis on digital rights, content licensing models, and affordable streaming platforms has reduced dependence on torrent-based access for many users. Where legal access is available, it typically offers greater security and stability.
Frequently Asked Questions (FAQ)
1. Is using a proxy site illegal?
Using a proxy itself is not automatically illegal, but accessing copyrighted material without authorization may be unlawful depending on local regulations.
2. Does a VPN make torrenting completely anonymous?
No method provides absolute anonymity. VPNs enhance privacy but may retain logs or be subject to legal requests.
3. Why are torrent domains frequently changing?
Domains change due to court orders, seizures, or proactive blocking by ISPs and regulators.
4. Is changing DNS enough to bypass restrictions?
It may work against DNS-only blocks, but it does not bypass IP-level filtering or provide encryption.
5. Are proxy mirrors safe to use?
Many mirrors are unofficial and may host malicious ads or modified content. Careful evaluation is important.
6. What is the safest way to obtain digital media?
Licensed streaming services, official stores, and open-source repositories provide the most secure and legally compliant options.
7. Why is torrent access slow when using certain networks?
Some anonymizing networks like Tor prioritize privacy over speed, resulting in slower connections.
In 2025, accessing blocked torrent platforms involves a mix of technical workarounds and risk management. While several methods continue to circulate online, none eliminate legal or cybersecurity concerns. Anyone considering such access should weigh privacy, security, and compliance carefully before proceeding.


Leave a Reply