Bruteforce attacks can be dangerous. They’re usually targeted at pages that have a form. In the case of WordPress, the login page of 1000s of websites is bombarded with brute force attacks every day. The attacks can keep the CPU of the server and database server busy and your site may crash or its features may not function. If you’re using weak login credentials, the attacker might also get access to your WP dashboard. To protect your website from such type of attacks or to make the attacks ineffective, you can use the following tools or plugins:
WordPress Brute Force protection plugins and tools
Fail2Ban
If you’ve got root/sudo access to the server, you can use Fail2ban to protect your WordPress website from brute force attacks.
Fail2Ban ships with several filters. To see the list of filters, navigate to the /etc/fail2ban/filters.d directory and run the below command:
ls -ltr
In case you don’t want to use a custom filter that you have designed or found somewhere on the web, you just have to enable the filter by editing the jail.conf file and adding the “enabled=true” option below the “service” or “application” you want fail2ban to monitor. For example, if you’re running a mail server, you can enable the Postfix filter by adding enabled = true below [Postfix].
Fail2ban will monitor the log file every “X” seconds/minutes and will ban the IP address that matches the condition specified in the filter every “N” times.
Fail2Ban uses Linux’s built-in firewall i.e. IPTables to ban IP addresses and it is very effective. Once you install and configure Fail2Ban, you won’t have to install a brute force protection plugin or worry about the attacks (unless you’ve set a weak password).
Fail2Ban saves its activities, the IPs it has found or banned in the Fail2Ban log file. This file is present in the /var/log directory.
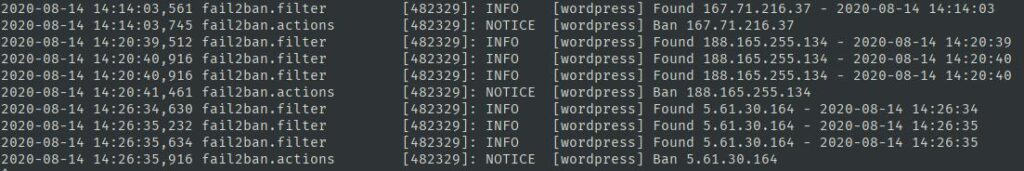
Fail2Ban is a sophisticated tool. In case you’re not able to set it up, you can use the following plugins:
Plugins that prevent brute force attacks.
No Captcha reCAPTCHA
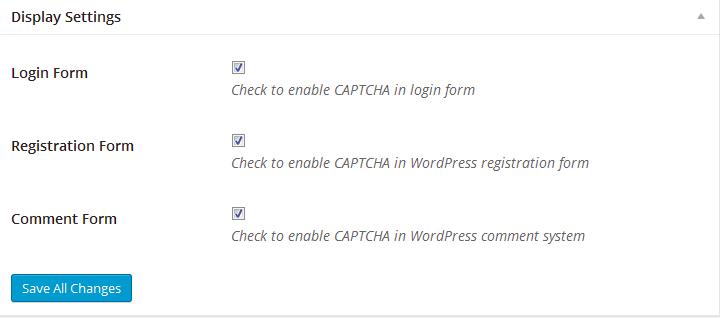
This plugin adds a captcha to the login, registration, and comment forms of the WordPress website. The “Log in” button will be disabled until you or the user who wants to log in to the WordPress dashboard solves the captcha problem. When someone bypasses the challenge, you’ll see a warning in the WordPress dashboard. Once you see the warning, you should check the website’s access log file and find out the IP that is responsible for the Brute Force attack. Once you find the IP, ban it using IPTables. This plugin won’t block the IPs but it will annoy the person who’s flooding your site with a brute force attack. As the “Log in” button won’t be activated unless the person solves the captcha challenge, the attack won’t be a successful one. However, you should keep an eye on the notice generated by the No CAPTCHA reCAPTCHA plugin.
Limit Login Attempts Reloaded
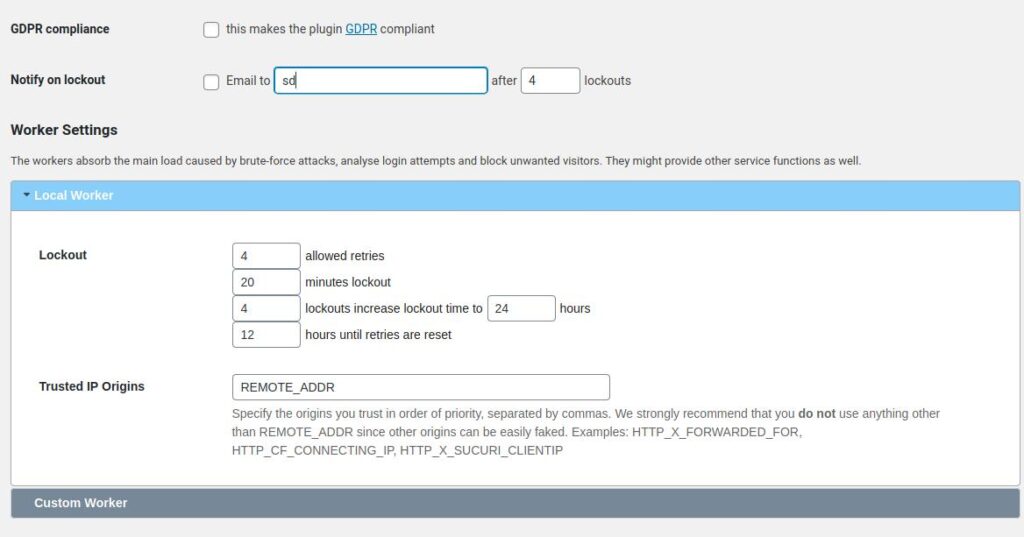
This plugin is similar to Fail2Ban but unlike f2b that users must configure themselves in the command line mode, this plugin offers a GUI based settings interface. Limit Login Attempts doesn’t have ads. This plugin lets you set the “Trusted IP Origins” and the following lockout parameters:
- Allowed retries, Number of lockout minutes.
- Hours after which the retries for IP addresses are reset.
The plugin has a “Statistics” section where you can see the number of IPs it has blocked and a list of IP Addresses. LLAR provides an option to make it GDPR compliant.
Loginizer
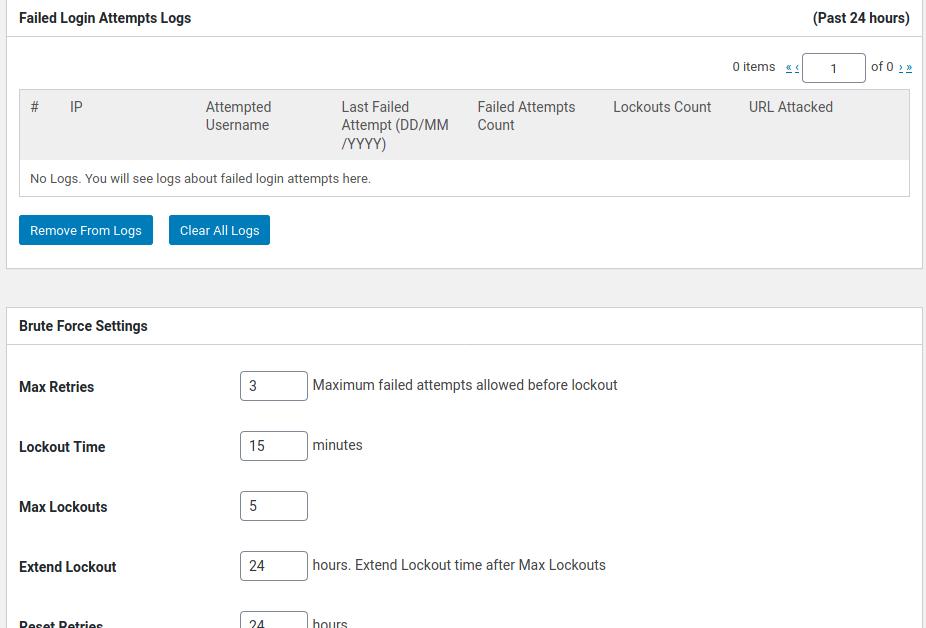
Loginizer is similar to the above plugin. It lets you set the following values:
- Max retries, lockout time, max lockouts.
- Extend lockout, reset Retries.
You can configure this plugin to send an email alert to you after it locks “N” IP addresses. If you know the IPs that are frequently targetting your website, you can blacklist them. To make sure that you’re not blocked from logging in to your website, you can whitelist your IP address in the Loginizer plugin.
Cloudflare
Cloudflare can detect and block internet threats. It checks the IP address of the visitors. If the IP is suspicious, the user will be asked to pass a captcha challenge to prove that he is a human. The captcha page is served by Cloudflare itself. Once the user passes the challenge, he’ll be able to access the page of your website.
I use Fail2Ban to protect my websites. The tool works great and it doesn’t affect the performance of the server. If you don’t have root/sudo access, use one of the 3 plugins I’ve shared above. You can also use Cloudflare.